Do You Have Employees Working Home?
Since Covid-19 work from home employees have a higher risk of insider threat and data loss than ever before.
If your employees are working from home, who is monitoring their user’s behavior?
Not all employees are equal when working from home. Do you really need to manage your endpoints?
“There has been a 41 % increase in data being stored on endpoints since the beginning of the COVID-19 pandemic.” Forrester June 2020
IT & HR policies must be administered today with real-time monitoring and behavior software to protect your endpoints. It becomes more critical as employees access and uses your sensitive data from home.
Over 50 % of data compromise is coming from your users! It is becoming one of the most significant threats to small and medium-sized businesses today. More, than half of all enterprise data now lives on endpoints, beyond traditional visibility and security tools centered on a network drive or central server.
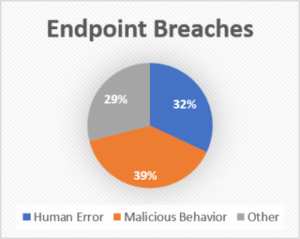
Human error accounts for over 32 % of sensitive data that mistakenly gets sent out. Another 39% is done with malicious intent by disgruntled employees. Half of the employees who left or lost their jobs in the last 12 months kept confidential corporate data, according to IT BUSINESS
EDGE, and 40 % plan to use it in their new jobs. The results show that everyday employees’ attitudes and beliefs about intellectual property (IP) theft are at odds with most company policies.
Sensitive data is at the core of all businesses, and protecting endpoints is quickly becoming a requirement of doing business. Regulatory compliance like HIPAA, PCI, GDPR, CCPA, SOX, NIST, and others can no longer be ignored or deferred as customers/consumers are demanding proof that their data is protected.
Trying to educate employees is good but, not a full proof or reliable solution. However, having data loss prevention (DLP) and endpoint protection (EPP) software that proactively monitors and manages the employee is the only solution. Reacting in real-time to human error or a malicious attack is a necessity.
User-behavior of an employee working from home
Most employees will take the easiest path to complete their work even if it means going around IT policies and downloading data to USB devices or saving copies to cloud-based storage like Dropbox, or using a personal printer attached to their home network.
To them, it is just a quick and easy shortcut to get what they need to be done.
What they do not realize is that these behavior’s put your company’s data at risk. Cybercriminals are trolling more than ever today for these types of user behaviors to gain access to your data and network.
Understand what users do from when they login to when they log out is the only solution to ensure the safety of your network data. The ability to protect against and detect an insider threat (Theft, fraud, data breach) becomes even more critical to the company’s data when employees work from home.
Companies that are dealing with regulatory compliances have a greater need to provide proof that data has been properly utilized and not compromised.
IT & HR policies do not have a bias towards the office, and having real-time 24/7 electronic enforcement is the only safeguard to ensure employees are not putting your business in jeopardy.
Having a solution that monitors and manages the user behavior with analytics is critical to any business with employees that work from home.
Prevent Data Breaches before they happen
The fear of the unknown encourages employees to take data. Everything from vendor files, pricing, customer list, drawings, formulas, and intellectual property is at risk and more. There is no hierarchy as to whom or when.
More than half of the employees who left or lost their jobs in the last 12 months kept confidential corporate data, and 40 percent plan to use it in their new position.
Quest research found 90% of organizations feel vulnerable to ‘insider’ data breach attacks, with excessive access privileges (37%), access to sensitive data (36%), and the increasing complexity of IT (35%) being the key reason why.
The reality is companies do not even know what their employees took. Cybercriminals know that there are four natural access point breaches in your network that all your employees have access to.
These employee data points are e-mail attachments, file uploads to a browser, removable drives, and printers. Many small to middle-market companies are unnecessarily exposing themselves every day to a potential breach and phishing attacks because of these four leak points.
Think about phishing just for a moment, how many times have you heard or read a story about someone clicking on a link? Employees that have access to the web, clicking around on social media sites, copying files to Google drive, or downloading an executable without even knowing the potential threat that they just exposed to your network.
Access to personal emails is another threat. It is a great way to expose your network to a phishing attack that can launch ransomware. It is also a quick way that employees can send sensitive files to themselves. A lot of sensitive data can be sent out via a personal email account.
We all love USB devices for their convenience and quickness to copy and share all kinds of stuff. Just ask Garrett popcorn how an employee downloaded 5,000 files of sensitive data and then left the company. They copied sensitive data to a USB and emailed files to their personal email account. Cybercriminals love USB devices because they know they get shared! Great place to hang out if you are a virus moving from one laptop to the next until they get access to your sensitive data.
The other common leak point is the printer as employees think if it is on paper, no one will know they just printed off the customer list, IP drawings, financials, or a vendor list. Just another soft target for access to that USB.
How could this breach have been prevented? The Solution
Armarius Software could have proactively prevented this breach from happening the second this individual inserted the USB and ensured that files in email never left the network! The software could have also alerted the company’s management or security officer of malicious behavior. You can protect trade secrets with Amarius Software Solutions.
Even if you allow some employees to have access to your sensitive data, shouldn’t you know what they are doing with that sensitive data?
If sensitive data and intellectual property are a critical part of your business, then securing the end node.
Armarius Software is the only real-time proactive software designed to protect your intellectual property and sensitive data from employee data breaches or anyone with malicious intent during and after the merger and acquisition process.
We also have the only software that is preventive SAAS solution that proactively monitors and manages in real-time your employees’ access to sensitive data and I.P. It can stop malicious behavior, record it and provide alerts before any data breach attempts can ever leave the network.
The software has a complete audit reporting feature set to prove that your I.P. and sensitive data has not been breached or compromised.
Unlike other IT solutions which only react after an occurrence has happened and can threaten your deal. The Armarius Software solution can prevent a data breach before it can occur. Even if an employee with good intentions, mistakenly tries to email sensitive content or attach a document, it will be stopped before it can be sent out.
It only takes one employee to jeopardize a deal by taking your sensitive data or intellectual property. Our software installs remotely in less than 30 minutes. As much as 70% of data breaches occur at the end node.
An easy-to-use real-time employee behavior monitoring and data loss prevention software. Set up your data protection policies and let the software monitor your remote worker’s online activities. You can then enforce and protect company data and rest assured that your policies are being followed by employees who work from home.
By automating and integrating all aspects of the DLP process, Armarius Software – SMS is able to provide powerful tools and built-in support to rival the big technology shops—but at a fraction of the cost.
Why wait for data loss to happen?

Today’s only data loss and user behavior software that goes with you wherever your office maybe
- Monitor and manage employees with user behavior software to secure your data.
- Meet regulatory data compliance,
- Electronically enforce IT & HR Policies
- Prevent human error
- Proactive stop malicious behavior
- Automate reports and alerts
About Armarius Software | Simply Secure Human Intelligence
We are Employee Productivity Monitoring & Security, Anywhere! Which is an affordable software-as-a-service hosted on your server or cloud platform. Our scalable industry-agnostic software solution is ideally suited for small to middle-market clients that have anywhere from 5 to 100,000 users. Our solution has proven its robustness in financial banking for over ten years. Any industry from manufacturing, distribution, services, retail, and more can use our software. Our software is used in highly regulated industries that required data compliance to meet SEC, SOX, HIPAA, NIST, GDPR, PCI, ISO, PII, CCPA, and others. We proactively monitor and manage user behavior, so your sensitive data and I.P. is never at risk.
Start right now to enforce in realtime your user’s behavior with IT & HR policies today by “Know now, what you need to know!”
Visit our website www.armariussoftware.com for your 20-minute demo or qualify for a free 30-day trial assessment of your users’ behavior. Armarius Software 1-331-305-3700 or sales@armariussoftware.com
Why should your cybersecurity be like a Swiss Army Knife?
Just like the individual tools of the knife, each one has its purpose and effective use. Some, however, can serve multiple purposes or uses you never thought you needed. Insider threats are very similar, you just never know what the next tool needed will be. This Swiss Army knife is
Working from home or anywhere proactively protect your data
Employee monitoring software regardless of where they work!
When does working from home = Productivity + Data Loss Prevention
Remote work or hybrid has become the norm, and ensuring employee productivity and data loss prevention is the new challenge. There are many solutions for employee monitoring software with features like time tracking, screen monitoring, and activity logging, and businesses can now gain a comprehensive understanding of how their remote
When is a User Activity Monitoring Solution Intelligent and Secure?
When it is an All-in-One software solution that uses proactive data technology to detect and stop insider threats, whether human error or malicious intent. Real-time visibility of monitoring activities on or off the network with 24/7 proactive detection User transparency, whether working from home, office, or anywhere Create an end
Would You Know If An Employee Was Taking Your Sensitive Data?
WOULD YOU KNOW IF AN EMPLOYEE WAS TAKING YOUR SENSITIVE DATA? Understanding user behavior is the easiest and most cost-effective way to prevent breaches. Right? Let’s see if we agree. Have you?: Set up IT & HR Policies
Protect Your Bottom Line
WOULD YOU KNOW IF AN EMPLOYEE WAS TAKING YOUR SENSITIVE DATA? Understanding user behavior is the easiest and most cost-effective way to prevent breaches. Right? Let’s see if we agree. Have you?: Set up IT & HR Policies